150+ Fake Mozilla Extensions — One Backend & Paid Media
Media blamed “Russian bears” for 150+ fake Mozilla extensions. Our findings show Nigerian infrastructure (IP 185.208.156.66), recycled phishing kits, and how paid articles helped spread the myth.
Background
A wave of headlines tied 150+ fake Mozilla extensions to a “Russian trail.” Our volunteer investigation shows these extensions relied on a single backend hosted on 185.208.156.66 — consistent with Nigerian scam infrastructure.
Key Findings
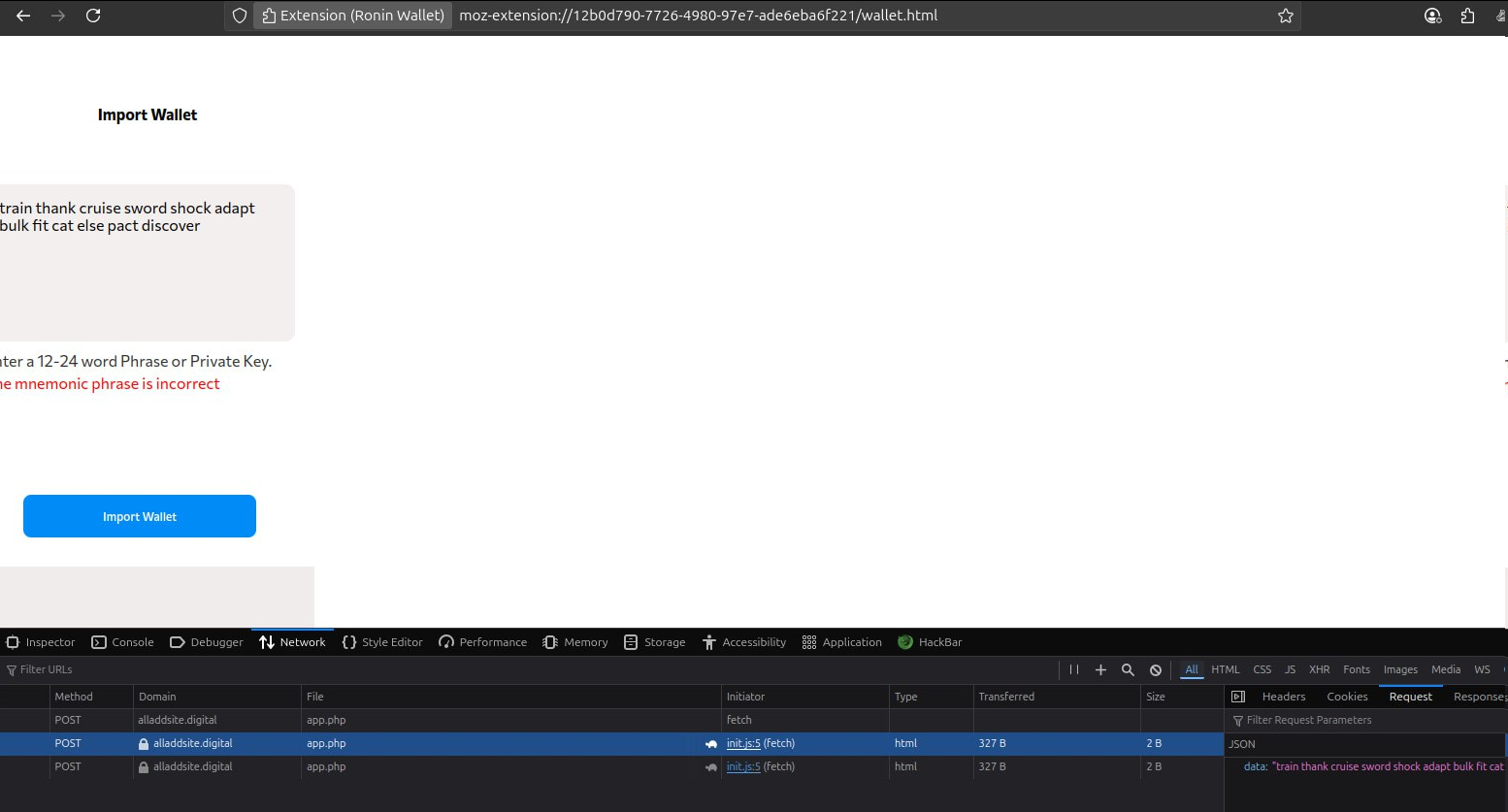
- Over 150 extensions reused identical low‑quality phishing kits.
- All communicated with a single backend on
185.208.156.66. - Neighboring domains on the same IP: bank scams, crypto scams, fake deliveries.
- A Telegram ID embedded in the code pointed to a Nigerian operator.
- Russian groups typically use distributed infra (Cloudflare Workers, Firebase, AWS) — not a single reused backend.
Evidence & Snapshots
Urlscan sample: https://urlscan.io/result/0198e619-7b76-74a0-b581-c2e788879572/. Many domains are dead now; urlscan/WebArchive preserve snapshots of what we reported.
Paid Media Problem
A single paid article in a large outlet becomes a seed; hundreds of smaller sites and Telegram channels rewrite/translate it, creating a wall of credibility that hides the truth. Victims stop reporting, investigations stall, and the real operators remain untouched.

Our Actions
- Submitted domains/extensions to Mozilla.
- Escalated links/evidence to SEAL for faster takedowns.
- Filed a public notice on ChainAbuse.
- Injected millions of empty seed phrases to waste attacker resources.
Disclaimer
We do not accuse any individual or outlet. All facts are open‑source and verifiable. The question is why such narratives are amplified — and who benefits when an unknown “security company” publishes an expensive, inaccurate investigation.