Scammers Are Mad: $0 Takedowns, Priceless Tantrums
Since 2019, our site started as a joke (“you don’t even have a website!” — scammers to a registrar). We built one in 15 minutes. The joke stuck — the takedowns scaled. We remove phishing domains & infra, preserve evidence for investigators, and avoid doxxing. When abusers get cocky and cross the line, we escalate and pass identities to authorities. They burn thousands. We spend $0. We laugh.

How We Operate
- Primary goal: remove phishing links & infrastructure fast.
- Evidence first: we snapshot sites (incl. Web Archive) before takedown to avoid harming investigations.
- No doxx by default: we don’t touch “the person” unless their escalation forces legal reporting.
- $0 model: automation + one SMTP report containing everything a registrar/host needs.
Why Scammers Fail (and Pay)
- Bulk inbox floods (2–5k msgs/day for months). We don’t wait for replies — no impact.
- Paper company stunts in the U.K. + forged “ownership” docs. Domain on a private person — claims fail.
- Braggy “law-enforcement style” social takedowns — irrelevant to infra removals.
- Illegal content swaps to trigger auto-bans — we don’t auto-post third-party content.
- Fake followers/likes/reports from bot farms — reported and wiped.
- DDoS attacks: expensive, pointless — email flows continue; the lander is optional.
Incidents (Screens & Pop-ups)
“Hacker panel” — visual parody
Not a product. Just an image to mock their UX obsession over crime dashboards.
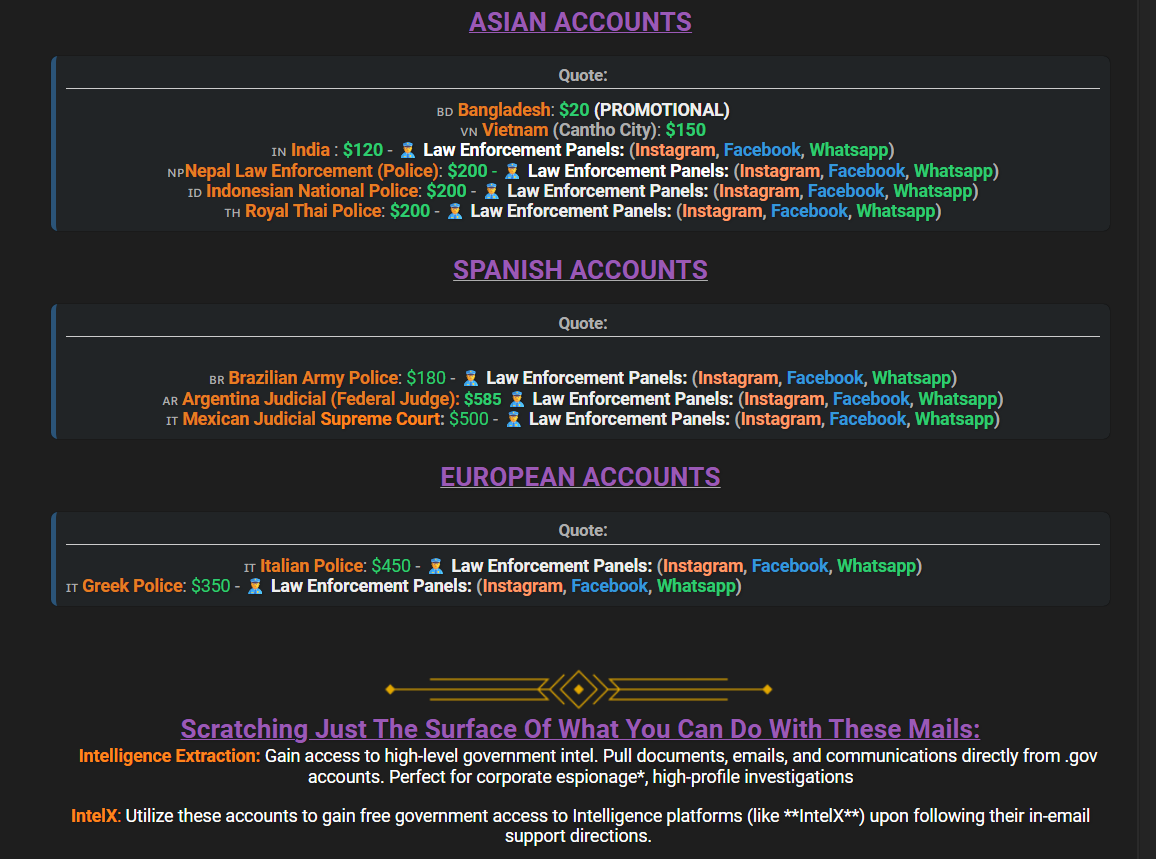
Forum Pricing - Their “gov access”
Pricing from public scam forums. Education only. They even do a turnkey service and have access to automated law enforcement dashboards.gov as normal.
Fake “Russian hacker” forums — marketing stolen clout
Scammers make faux-RU boards and parade our work as their “service”. Screenshot preserved.
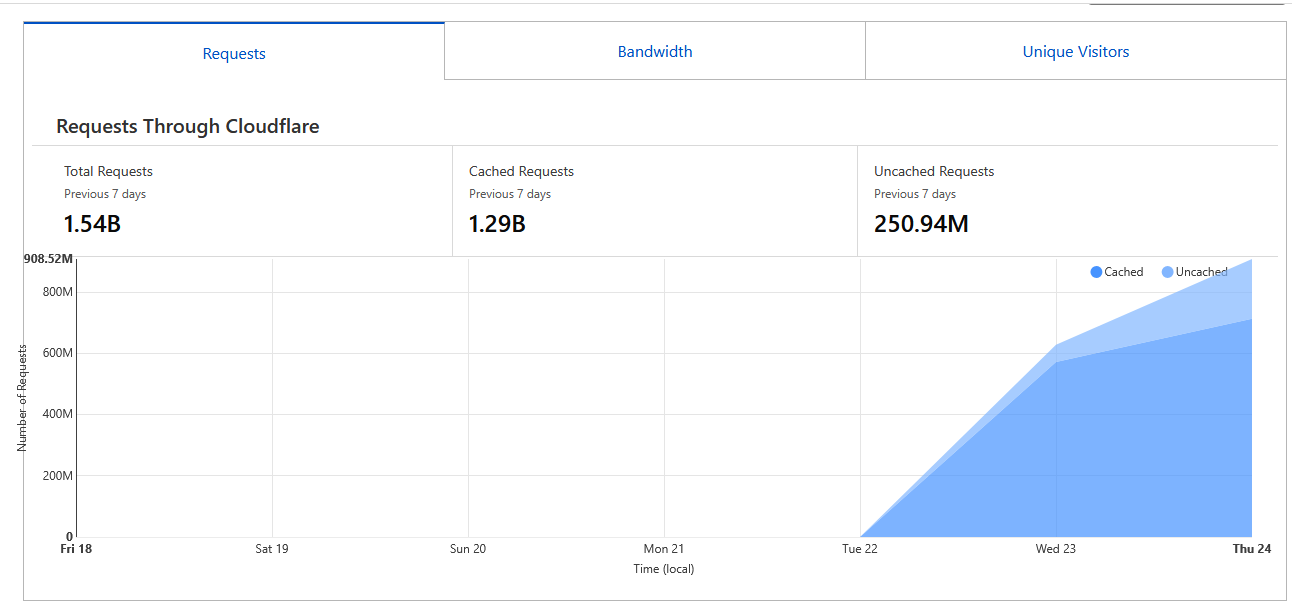
DDoS attempts — costly, irrelevant
They rent botnets to “drop” us. Email/takedowns unaffected; lander optional.
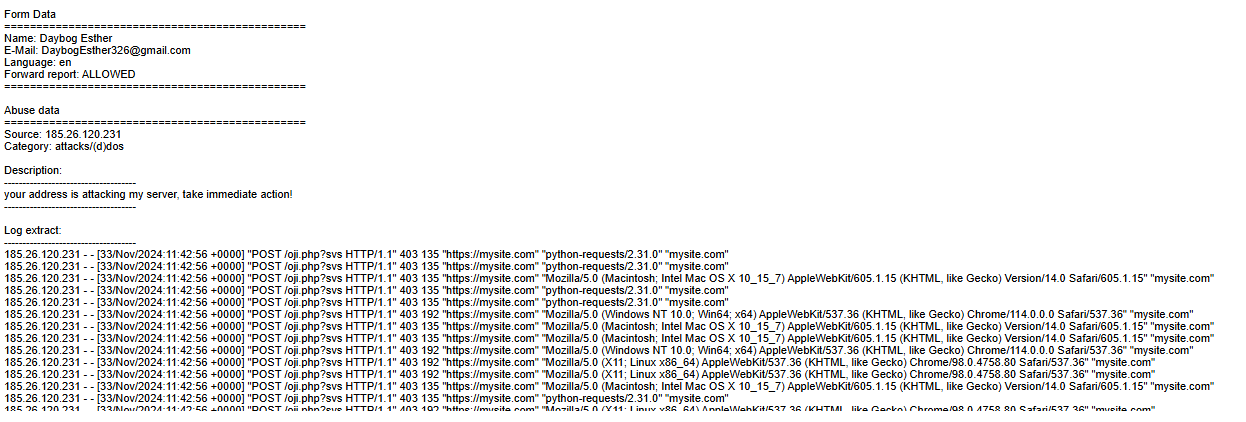
False report example — hosting confusion
[33/Nov/2024:11:42:56 +0000] "POST /oji.php?svs HTTP/1.1" 403 192 "https://mysite.com" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36" "mysite.com"
They hid the real domain as mysite.com in a report. It wasn’t DDoS but their seed-capture auth. Lessons were learned.
Social Media Takedowns & Archives
Our social accounts are often mass-reported. The CarlyGriggs13 X account was a ~$0.30 handle we used to auto-post ~140k takedowns for indexing. Our Medium blog faced a similar fate. Both were suspended. Here are the archives:
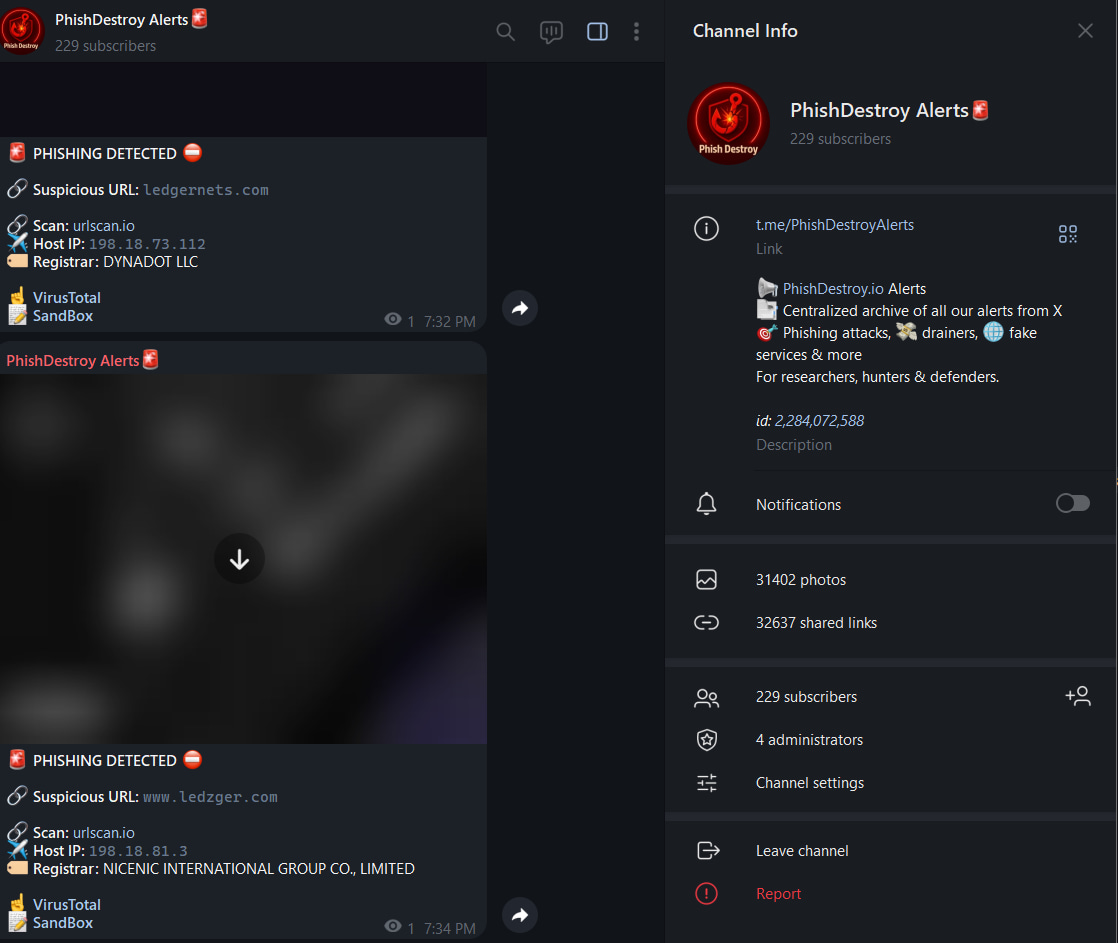
Telegram Channel Takedown
On September 3, 2025, they successfully mass-reported and took down our Telegram channel, where their domains were published for automated banning.
X (Twitter) Archive
GitHub RepoMedium Blog Archive
View ArchiveEvidence Preservation
- We store pages on public archives before takedown to keep the best possible evidence trail.
- When identity is clear and escalation is harmful, we pass to authorities — by the book.
- We prefer automation and infra removal to person-centric hunts.
Registrar responses vary. Namecheap consistently acts fast; others... less so.
$0 Policy, Real Impact
- Automation kills portfolios faster than “PR wars”.
- They spend on companies, bots, “legal” faxes, fake claims, and DDoS noise. We still remove their infra.
- Illegal threats ⇒ we escalate to law enforcement.
Want to Help?
Report a Domain
Closing
We warn them: “your infra turns off soon” — chaos begins. Meanwhile we keep it boring: scan, archive, report, remove. $0 spent. Impact compounding.